HOWTO: Find Out if a Vulnerability/CVE is Fixed in Solaris
I'm part of the Security Certified Group of engineers at Oracle and one of the most common questions that comes up is...
Is there a fix for CVE-####-## for Solaris #?
9 times out of 10, you can answer this for yourself, you just need to know where to look.
First, you need to determine whether the CVE affects a Oracle product directly (eg Solaris), or a third party product included with an Oracle product (eg Adobe Flashplayer as supplied with Solaris).
Once you have determined this, you can then determine where to look.
Oracle Products
There are two ways to determine if a particular CVE for an Oracle product has been fixed:
The Long Way
- Go to the Map of Public Vulnerability to Advisory/Alert page
- Locate the CVE
- Click on the Critical Patch Update link to the right of the CVE number
- Follow the link to the Oracle product you are querying
For example, to see if there is a fix for CVE-2010-4435 on Solaris 10, you'd...
- Go to Map of Public Vulnerability to Advisory/Alert page
- Locate CVE-2010-4434
- You'll instantly see this is resolved for the first time in the January 2011 CPU. Click the Oracle Critical Patch Update January 2011 link.
- On the page that opens, click the "Oracle Sun Product Suite" link which will take you to Document 1273260.1 which maps the CVEs to patches for each OS release for that CPU
As a general "best practice" you should review the quarterly CPUs as and when they are released so you can assess if you should be applying the CPU or not. This of course should tie in with your own patching practices. The Oracle Solaris 10 Recommended Patching Strategy white paper (PDF) has more details on helping your devise a patching strategy for your environment. You should review this in conjunction with the Critical Patch Update Implementation Best Practices white paper (PDF).
And don't forget, CPU Patchsets are cumulative. That is the January 2012 CPU will have all of the patches and fixes documented in all of the earlier CPUs, it will however only document those issues fixed in that CPU for the first time.
The Short Way
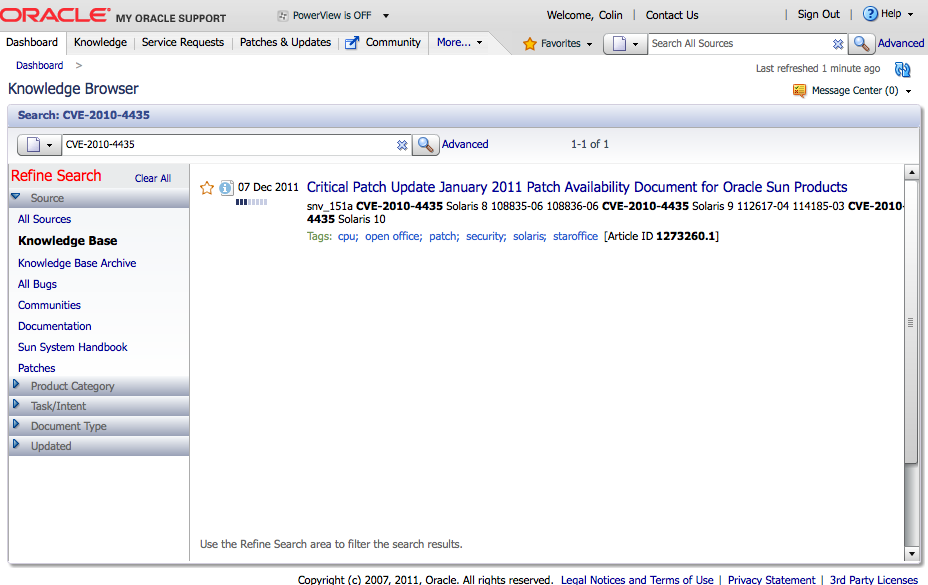
Simply search for the CVE number within My Oracle Support. Generally, the first search result will be the Patch Availability Document located using the long method above.
In the example used above, searching for CVE-2010-4435 within My Oracle Support, returns one result - Document 1273260.1 - the same document we identified above in the long method.
Third Party Products Included with Oracle Products
Oracle only documents fixes for security issues in the code/products it has full control over in the Critical Patches Update. All third party products fixed will be documented on the Vulnerability Resolution for Third Party Software in Oracle Products page.
Searching for one of the CVEs on this page within My Oracle Support will generally not return any results.
Fixes for third party products included with Oracle Solaris will also be announced on blogs.oracle.com/sunsecurity.
Disclosure Policy
At this point it is important to take note of Oracle's Disclosure policy which states:
In order to prevent undue risks to our customers, Oracle will not provide additional information about the specifics of vulnerabilities beyond what is provided in the Critical Patch Update (or Security Alert) advisory and pre-release note, the pre-installation notes, the readme files, and FAQs. Furthermore, Oracle provides all customers with the same information in order to protect all customers equally. Oracle does not provide advance notification to individual customers. Finally, Oracle does not develop or distribute active exploit code (or proof of concept code) for vulnerabilities in our products.
This means as a general rule, Oracle will not confirm or deny that any of its products are affected by any vulnerability/CVE until such time as it is publicly announced in one of the above locations. So if you can't find a particular CVE, it could mean one of two things:
- The Oracle product is not vulnerable to the issue
OR
- It might be, but there is no fix for it.
Unfortunately, at this time, Oracle does not officially document when its products are not affected by a certain vulnerability, but this may change in the future.
If all of the above seems vaguely familiar, it is because it is effectively a nice user friendly summary of the information detailed on or linked from Critical Patch Updates, Security Alerts and Third Party Bulletin. This is definitely a page for the bookmarks.