Oracle Now Releasing Critical Patch Update Advisories in CVRF Format
It's July, so time for Oracle to release a new quarterly Critical Path Update (CPU) advisory - July 2012's is here. If you've come from a Sun background, you should be used to Oracle's CPU release cycle and everything that is involved in it by now. All of that still stands, however as of July 2012, Oracle is now also providing the advisories in an XML format that conforms to the Common Vulnerability Reporting Format (CVRF) version 1.1 spec.
So what does that mean for you? Well, if you happen to have a centralized tool that parses CVRF reports from the likes of Microsoft, Cisco and RedHat and presents a nice report, you can now add Oracle to your list of supported vendors. The link to the CVRF for each CPU advisory will be at the end of the HTML advisory, so simply locate the URL and add it to your tool.
Now CVRF is designed to be machine readable, hence it is in XML, but if you don't have a CVRF parser but still want to see the report, you can. Oracle's CVRF report includes a stylesheet so you can view the report (July 2012's is here) in a web browser and it looks pretty good too:
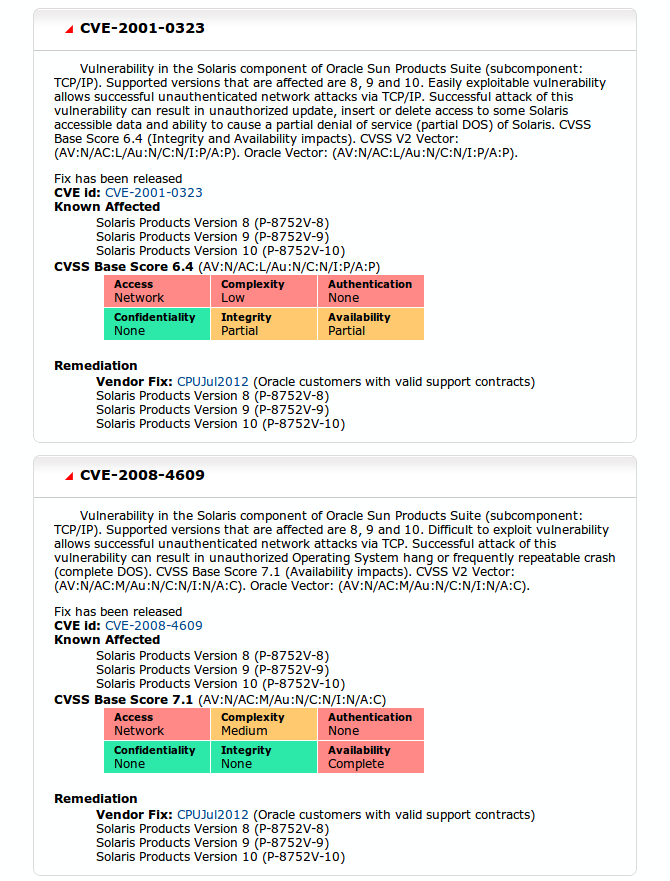
As you can see, some simple colour-coding allows you to quite quickly assess the severity of a vulnerability (based on the CVSS base score, without locating the score.
It's interesting that the report is currently marked "BETA" so I suspect the powers-that-be haven't decided entirely on the content or delivery mechanism, but given the report conforms to the CVRF spec, the actual format of it shouldn't change.
One thing I find a bit lacking, and it's something I'm not too happy about with the normal advisories is they don't tell you the exact patch that fixes a particular CVE, just the patchset. If you want to know the exact patch, you still need to refer to Doc ID: 1448883.1.
That aside, I think this is probably a very useful development for security administrators.